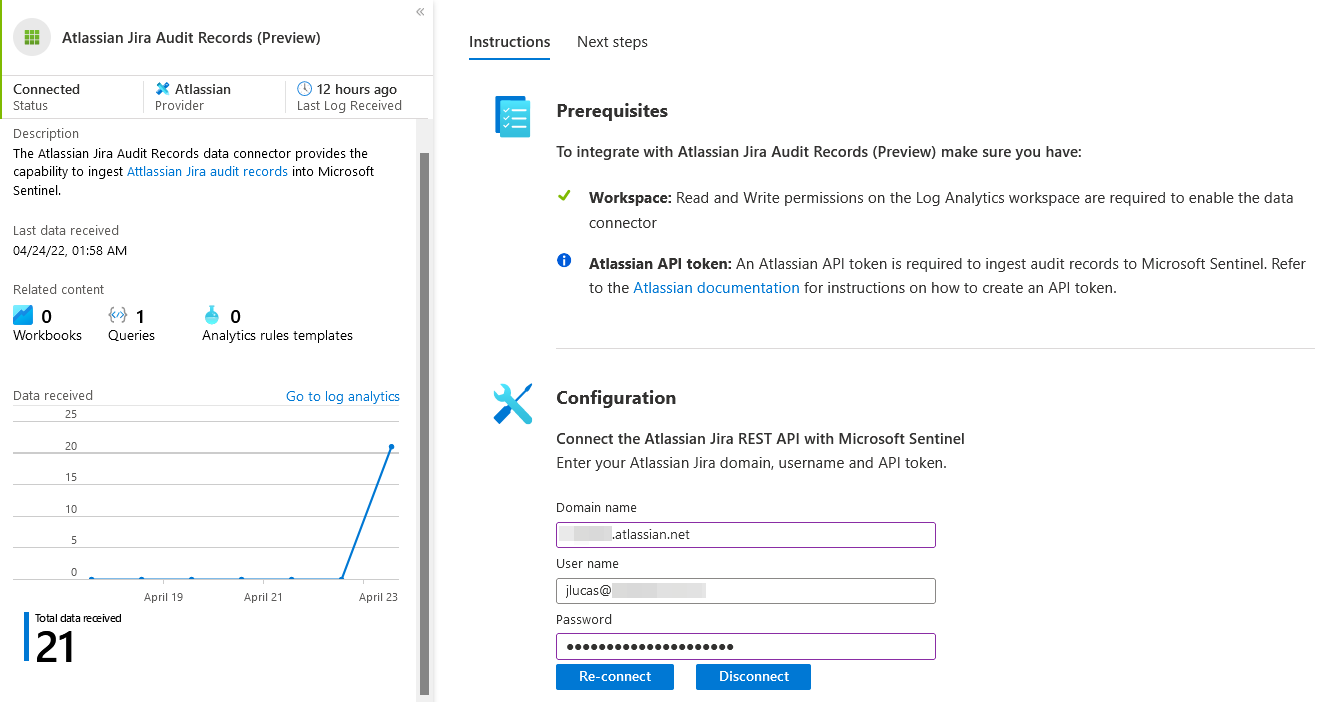
Creating a codeless data connector for Microsoft Sentinel
In this post we'll explore the process of using the new Codeless Connector Platform (Preview) to ingest Atlassian Jira audit logs into Microsoft Sentinel...

In this post we'll explore the process of using the new Codeless Connector Platform (Preview) to ingest Atlassian Jira audit logs into Microsoft Sentinel...
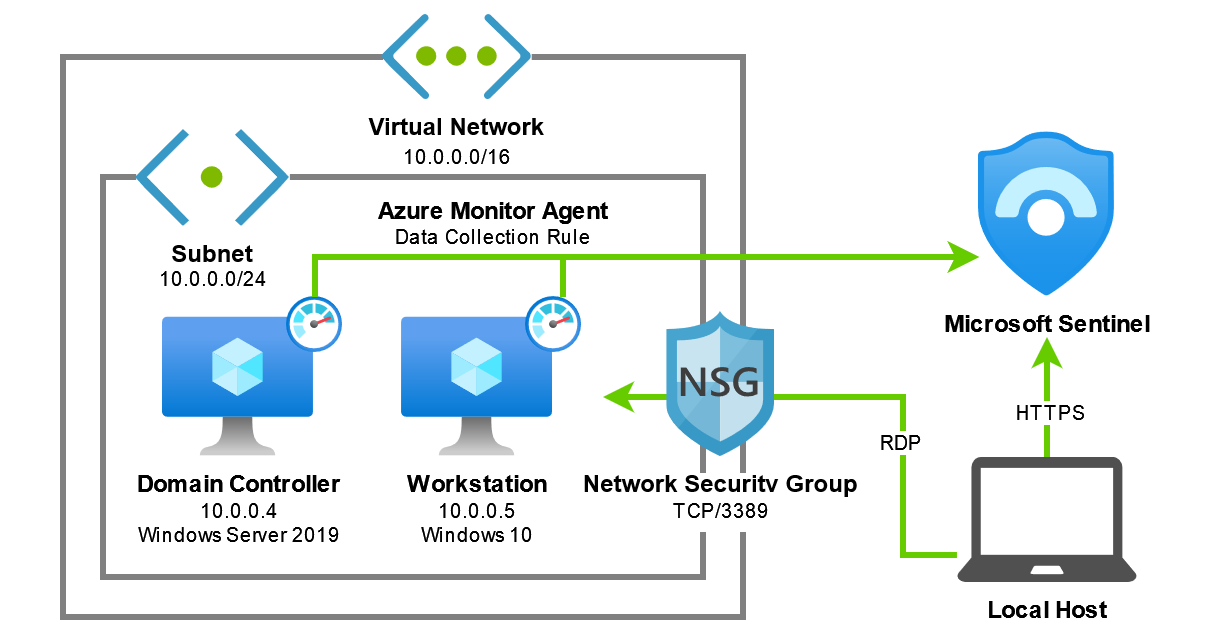
In this post we'll explore using Bicep to automate the deployment of a Blue Team lab environment in Azure consisting of an Active Directory domain, Microsoft Sentinel and the Azure Monitor Agent...
In this post we'll explore using privileged access groups to implement time-based conditional access policy exclusions and impose app enforced restrictions in SharePoint and Exchange Online...
In the final part of this series we'll write a script to generate vulnerability reports via the Microsoft Defender APIs, and deploy the result to Azure Automation...
In this two-part series we'll create an app that sends automated vulnerability reports directly to your users via the Microsoft Defender for Endpoint APIs...